HOWTO use CloudBerry Lab Remote Assistant in a secure and efficient manner
Contents
Introduction.Abbreviations.
Why would I need to use CRA?.
CRA versions.
How is the tutorial organised?.
How Do I…
Run Remote Assistant Quick Support (applies only to CC).
Install Remote Assistant Full Version (applies to AC and CC).
Prevent a computer from being a CC (applies to AC only).
Harden / Restrict access to the CC (attended mode).
Only share an application on the CC (attended mode). Enable hardened unattended access to the CC.
Configuring CRA.
Enable encryption.
Setting the PIN length / duration.
Enabling unattended access.
Setting the type of access for incoming connections.
Prompt for incoming connections.
Share a specific application.
Prevent CRA from accepting new connections.
Installing CRA.>
Remote assistance and hack attacks.
Introduction
CloudBerry Lab is a company better known for its backup solutions and if you’re in the market for such a product you should check out their offerings. This article is about CloudBerry Remote Assistant. CloudBerry Remote Assistant is a hidden gem because it is a highly functional free product that allows one computer (or IOS currently in Beta) to connect securely to a second computer. The two computers must be connected to the internet.In a world in which words and phrases can take on a different meaning by simply appending an asterisk at the end and writing some fine print in some corner of the page, the free when applied to CloudBerry Remote Assistant take on the traditional definition: no stings, no exceptions free.
This is a tutorial on how to securely use this program to cater for different situations you might encounter. Although not every option is discussed, it will cover the most common use cases.
Abbreviations
CRA
|
CloudBerry Lab Remote
Assistant
|
The program this tutorial is
about
|
AC
|
Accessing Computer. Within
CRA this is the “Control Remote Computer” device.
|
This is the computer that
initiates the connection and will control or view the resources of the host.
|
CC
|
Controlled Computer. Within
CRA this is the computer that “Allows Remote Control”.
|
This is the host computer
whose resources are controlled or viewable on the connected AC.
|
Why would I need to use CRA?
Any situation in which one computer may need to view or control another computer falls within the remit of CRA. The following use-cases further clarify the topic RAC can address:- Support. The person at the CC requires assistance to perform a task or diagnose an issue. Rather than physically bring in a person to look at the problem, the person at the CC grants access to the person at the AC. The person can be a professional or the family guru everyone calls when the printer is not working. Problems do not necessarily need to be computer tech issues although they must be sharable on the CC—check out Khan Academy @ https://www.khanacademy.org for a non-tech example.
- Demos and Training. The person on the CC is conducting a product demo with a prospective client who is following the demo on his AC. The client connects to the CC in view-only mode to follow the actions taking place on the CC and better understand how the product will address his needs.
- Collaboration. Two persons can meet on the CCs computers to work together on a task.
- Unattended access. The cases presented above assumed that the person using the CC be physically present in order for the connection to take place. In unattended access the CC is configured so that authorised people can connect without the need for a person to be present at the other end. A use case is to access an office computer from home or a home computer from the office.
- File transfer. Once a connection is established between the two computers, files can be transferred between the two computers. Unless unattended file transfers are enabled, file transfers requires acceptance by people at both ends.
- Chat and Voice functions. These functions are built into the program primarily to compliment the use-cases discussed above. Once a connection is established, actions or procedures being performed can be explained. This greatly enriches the overall experience of the session.
CRA versions
CRA comes in Full and Quick Support versions. The full version is necessary for the AC. The CC can use either version. The table will help you choose which version applies to you.How is the tutorial organised?
This remainder of this tutorial is organised into a- How Do I… explains how to perform certain tasks. The explanations focus on configuring the product to be as secure as possible. This steps link to the different configurations that are necessary to perform the required actions. A person who is comfortable navigating CRA’s menu structure can focus on setting up the necessary parameters without the need to consult the actual configuration section of this tutorial.
- Configuring CRA… goes into the configuration screens of CRA providing a walkthrough. The topics in this section are referenced by the How Do I… section.
How Do I…
Run Remote Assistant Quick Support (applies only to CC)
You may need/want to run Quick Support option because:- Your computer administrator blocks your ability to install programs on your computer;
- You are an infrequent user and prefer to install it only when you need it;
- You are security conscious or not very technical and prefer not to risk having the CRA running or misconfigured after you’ve finished with it.
- Install CRA
- When Remote Assistance Quick Support is run you are presented with two values: the Computer ID and a PIN. These need to be communicated to the person sitting at the AC so that he can link up.
Install Remote Assistant Full Version (applies to AC and CC)
The full version of CRA:- is the only option if you are acting as the AC;
- provides more secure functionality than Quick Support;
- is mandatory if you want to use your CC in unattended mode;
- provides more granular functionality with respect to the location of log files and chat logs (not discussed in this tutorial).
- Install CRA.
- The various security-related functions are discussed elsewhere in this tutorial.
Prevent a computer from being a CC (applies to AC only)
This function is only available in the Remote Assistant Full VersionPath:
If you do not wish CloudBerry to receive incoming connections you can disable this functionality. Blocking incoming connections enhances the security of your installation.
Harden / Restrict access to the CC (attended mode)
Such a setup is applicable when the person
at the CC is demonstrating an action to the person at the AC with the latter
only viewing the actions. This view-only restriction is also valid in those
situations in which the trust level between the two ends is not sufficient to
grant the AC full control of the CC. In
such a scenario the person on the AC would communicate via voice or chat
instructions what the person at the CC should do. As the actions are being
executed, the AC can guide the actions through voice / chat.
If full control is/becomes necessary, it can
be revoked by the CC at any time.
Steps:- Enable encryption.
- Increase the PIN length and reset the PIN frequently.
- Give the AC view-only access to the CC or set the type of access every time a connection is established.
- Decide if you need to share the entire CC or a single application running on the CC (See Only share an application on the CC).
- Unless you expect other AC’s to connect, stop CRA (immediately or after a period of inactivity).
Only share an application on the CC (attended mode)
Limiting what is shared with the AC enhances security because it prevents the AC from looking at objects that are not of interest.Steps:
- Enable encryption.
- Increase the PIN length and reset the PIN frequently.
- Load the application that is to be shared.
- Prompt for the application to be shared.
- Unless you expect other AC’s to connect, stop CRA (immediately or after a period of inactivity).
Enable hardened unattended access to the CC
In unattended mode the AC can access the CC either by using the CCs login credentials or by entering the PIN generated on the CC. The option to periodically reset the PIN should be unchecked if unattended access will take place via this method. Either option can be used interchangeably. Unattended access only supports Full control access.- Enable encryption.
- Enable unattended access.
- (a) If you intend using the PIN to log into the CC, Increase the PIN length but disable resetting the PIN.
- (b) If you will not be using the CC’s login credentials rather than the PIN, Increase the PIN length and reset the PIN.
- When the AC connects, CRA prompts for valid computer credentials of the CC. To use the PIN, the person at the AC needs to click the link “Access using PIN”.
- At the end of the session, the AC can set what happens to CRA. The available options are:
- Sign out. All open programs are closed and removed from memory. This is the most secure option.
- Lock the session. This option keeps the existing session open but requires authentication to login again. Existing open programs remain in memory. This option is useful when the CC is being used to perform a lengthy process. Periodically the AC will log in to see the state of the process.
- Leave the session open. This option is very insecure because it essentially leave the CC unlocked. Anyone with physical access to the computer can execute any program or copy data from it. This option should not be used.
Configuring CRA
Enable encryption
This function is only available in the Remote Assistant Full Version.This configuration only applies on the CC.
Path:
Encryption generates a unique private / public key pair on the CC so as to encrypt communication. Every AC that wants to communicate with this CC will be prompted for its public key the first time it connects. By encrypting the session no one can eavesdrop the traffic.
The generated public key needs to be securely shared with the ACs that need to connect. If the key is compromised a new key pair can be regenerated. Regenerating a new key pair invalidates the previous public key.
On the CC, the encryption status is displayed on the Allow Remote Control screen.
Setting the PIN length / duration
This function is only available in the Remote Assistant Full Version.This configuration only applies on the CC.
Path:
The Quick Support option defaults to a PIN length of 4 characters and the PIN automatically resets every time the program is started. With the full version you can increase the length of the PIN to 10 characters. You can also specify whether the PIN changes periodically. Enabling this setting ensures that PINs will expire.
Longer PINs ensure that anyone attempting a brute force attack will have to work through a longer combination of values thereby making the task much more difficult.
Resetting the PIN causes a new PIN to be generated periodically. Brute force attacks become impossible because the PIN does not remain constant. Resetting the PIN also ensures that AC users cannot access a CC if the PIN has changed. For example in product demonstration environments, the PIN is reset every few minutes to ensure that the pin given out to a client at the AC will no longer work after the session ends.
You should reset the PIN only if there is a person at the CC end to read out the new pin, otherwise the CC cannot be accessed.
Enabling unattended access
This function is only available in the Remote Assistant Full VersionThis configuration only applies on the CC.
Path:
When enabled, the AC will need to know the CRA Computer ID. The program displays whether unattended access is on or off in the Allow Remote Control Screen.
Setting the type of access for incoming connections
This setting only applies when Unattended Access is off.This configuration only applies on the CC.
Path:
By default incoming connections can only view the screen. During the session the AC can request to the CC to be granted full access. At any time, the person on the CC can revoke Full Control by pressing the Alt-Pause key combo.
Prompt for incoming connections
Path:This configuration only applies on the CC.
This setting only applies when Unattended Access is off.
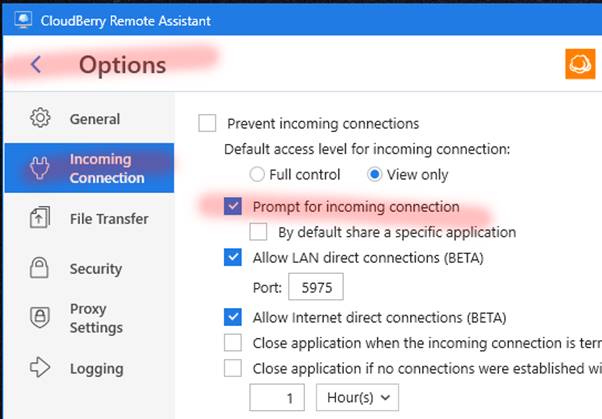
When this option is checked, every connection attempt will generate a prompt on the CC that requires the person to define the type of access. The person can, through the advanced settings, further control the session.
Share a specific application
This setting only applies when Unattended Access is off.
This setting can only be selected if Prompt for Incoming Connections is checked
Rather than share the computer desktop and all running programs, it is possible to share just one application. This is ideal for demos and tutorials as it allows the CC to focus on the application being discussed. It also does not show other running applications as well as desktop icons, etc.
The application that is to be shared must be loaded before the CC connects.
Checking the “By default share a specific application” prompts the CC to choose the application. Alternatively one can click on the “Show advanced settings” in the “New Incoming Connection” dialog box and selecting the application that can be shared.
Prevent CRA from accepting new connections
Path:CRA can unload itself after the current session terminates or after a predetermined period during which no new connections are established.
Installing CRA
To install CloudBerry Lab either google the term “CloudBerry Lab Remote Assistant” or head to https://www.cloudberrylab.com/remote-assistant.aspx. Navigate to the page from where you can download the Full or Quick Support version. A default install is assumed for the purpose of this tutorial. You will need an email address as part of the installation process.Remote assistance and hack attacks
You should never grant cold callers access to your computer. It is common practice for scammers, posing as tech support of a computer company to call you out the blues to inform you that your computer came on their alert radar because it has some serious bad stuff that needs to be fixed. Unless you remove this malware immediately you can be liable for prosecution and they will be disconnecting you for the internet. You need to act now. All you need to do it to install a program from a website they will provide at which point they will remotely access your computer and clean up the issue. In a few minutes they promise that all the matter will be resolved.These criminals use the standard scammer’s recipe; find a victim, present oneself as an authority (Microsoft tech support), frighten them (legal action), tell them that you are taking away something important for them (internet access), create a sense of urgency and give them a service for free.
Those who fall victim to this type of scam end up having their computer hijacked and will end up paying a lot of money to get back their computer and files, photos and other documents to where it was originally.
CloudBerry Remote Assistance as well all other well designed Remote Assistance programs build in safeguards to ensure that scammers will not gain access to your computer unless you let them in. You need to make sure that you do not end up being the weakest link.
I experienced a case in which the (soon-to-be victim) was frightened so much by the scammer that he guided the scammer on the remote assistant tool he used to grant full access.
The following guidelines should help you stay safe:
- Don’t react to cold callers;
- Never grant people you do not know access to your computer;
- Never install any program by anyone claiming to be from tech support (unless you initiate the service call);
- Never engage cold callers;
- If the cold callers manages to convince you that your computer is infected, take the computer to a local computer centre to have it checked;
- Research the topic.


















Great Content. Really Informative and Helpful. Thanks for sharing it with us. Appreciate it. Must check CloudBerry Remote Assistant Review
ReplyDelete